Shadow IT
Gain control over shadow IT
Shadow IT refers to any IT asset unknown by your IT team, including applications purchased by individuals, open source and free applications, and EOL applications still in use. Left unaddressed, Shadow IT opens your organization to application sprawl, security risk and surprise bills. Flexera helps you uncover Shadow IT and put governance in place to mitigate this significant source of potential risk.
Recommended Products
Uncover shadow IT to mitigate risk and wasted spend
Uncover shadow IT
Full visibility to mitigate risk
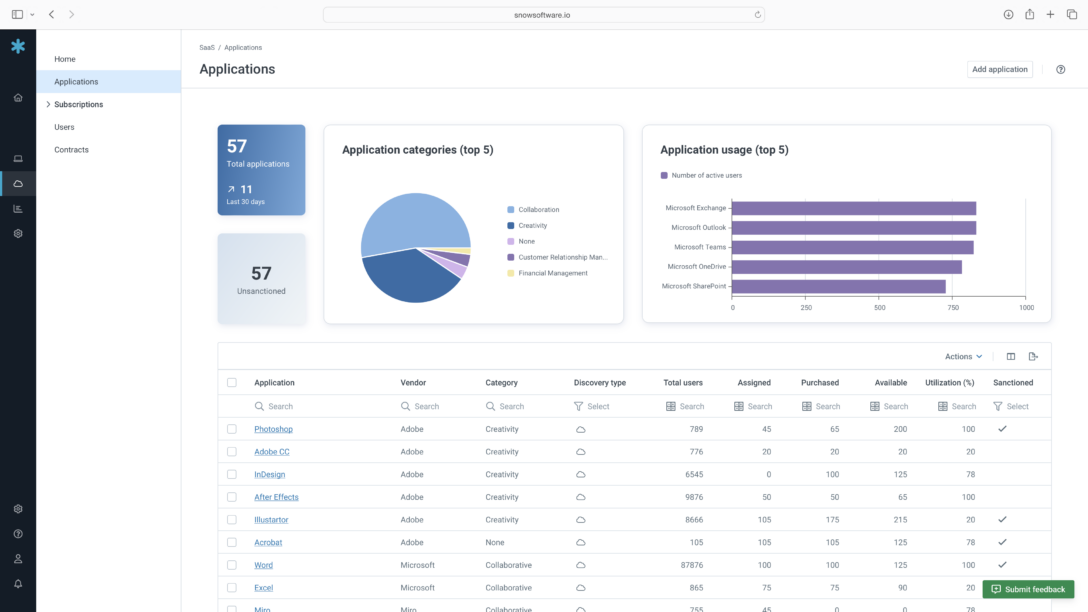
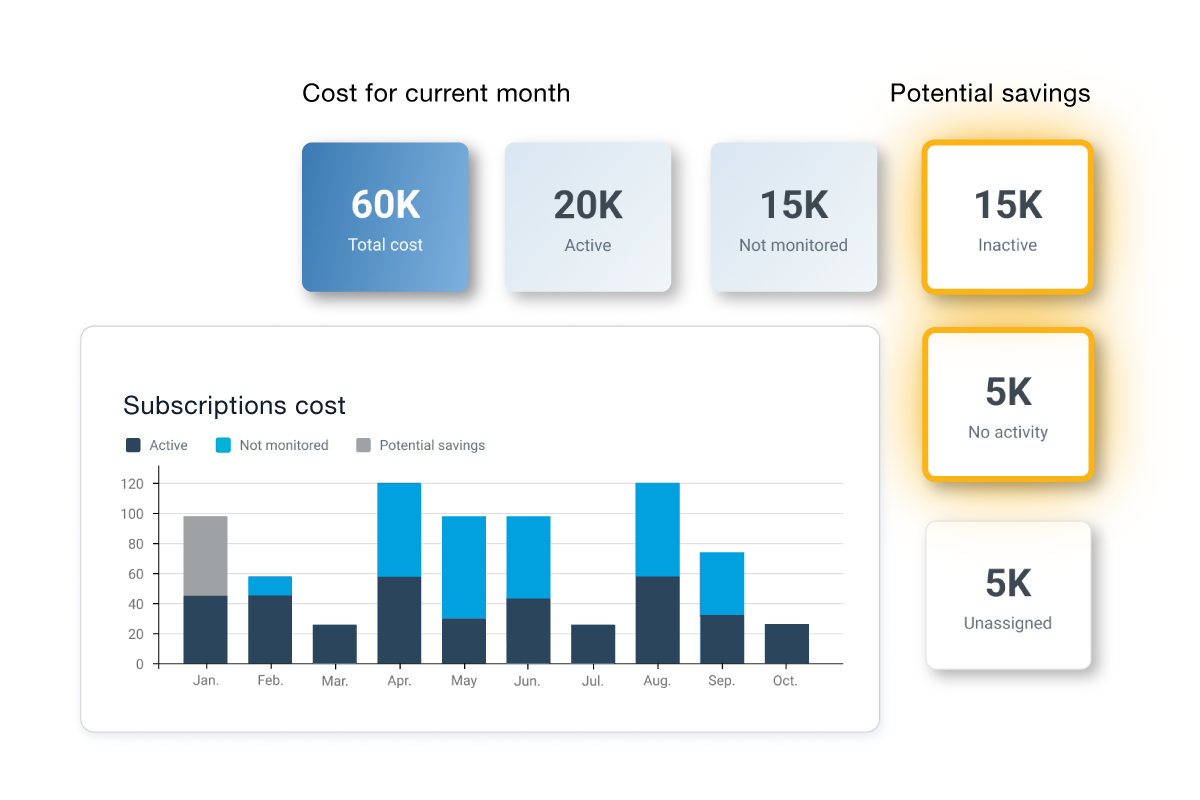
Without a comprehensive view of SaaS applications throughout your organization, shadow IT can run unchecked and leave your organization open to security risk, application sprawl and wasted spend. Flexera delivers the full visibility you need into the entirety of SaaS applications – regardless of whether they’re licensed, approved or authorized - so you can identify and take action on shadow IT, mitigating the risk of unknown SaaS resources.
Secure SaaS accounts
Eliminate business change risk
As employees come and go or their roles change, shadow IT can present itself as newly insecure SaaS. Flexera can help you place governance around usage rights for current employees, disable access automatically for anyone who has left the organization, and protect against unauthorized access to your proprietary data.
Identify risk
Find unvetted SaaS applications
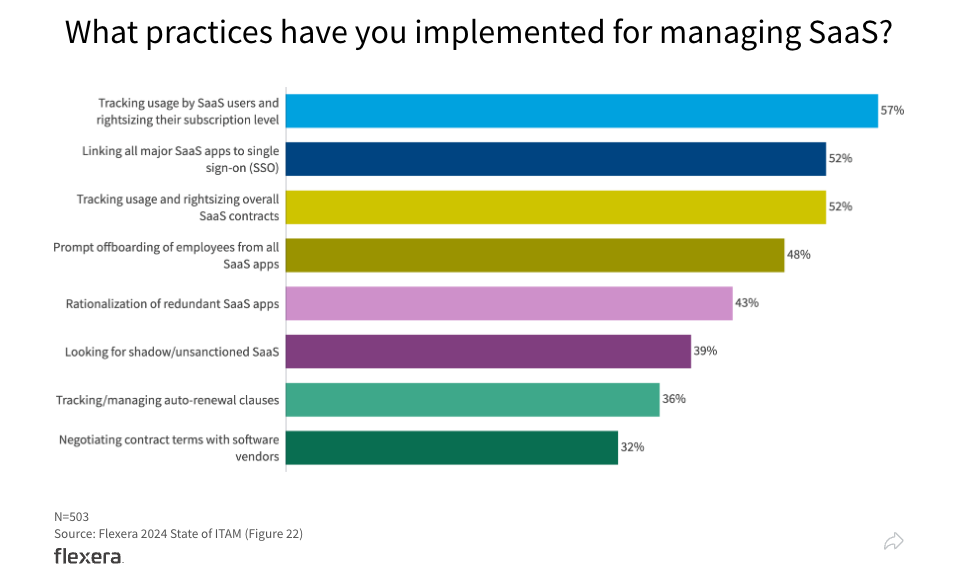
Individuals and business units can circumvent traditional procurement practices to use free and paid SaaS applications that your IT security team has not vetted. This opens the door to security risks and unexpected costs. Multiple highly effective discovery methods, including browser extensions and financial records, help find all these additional applications, enabling you to mitigate this risk and act on Shadow IT. As the software market changes rapidly, true comprehensive discovery is necessary to secure your SaaS applications from Shadow IT risk.
Shadow IT visibility
Bring light to Shadow IT risk
Full discovery is necessary to uncover Shadow IT. Reliable and comprehensive discovery methods are essential to uncovering SaaS usage that has bypassed security vetting throughout your organization. Flexera understands that effectively uncovering Shadow IT requires full visibility through multiple discovery methods to gain a comprehensive view of SaaS usage, both sanctioned and unsanctioned to mitigate security risk and wasted spend. Flexera combines multiple discovery methods to give you full visibility into which tools business units use, who is using them and what data the tools can access.
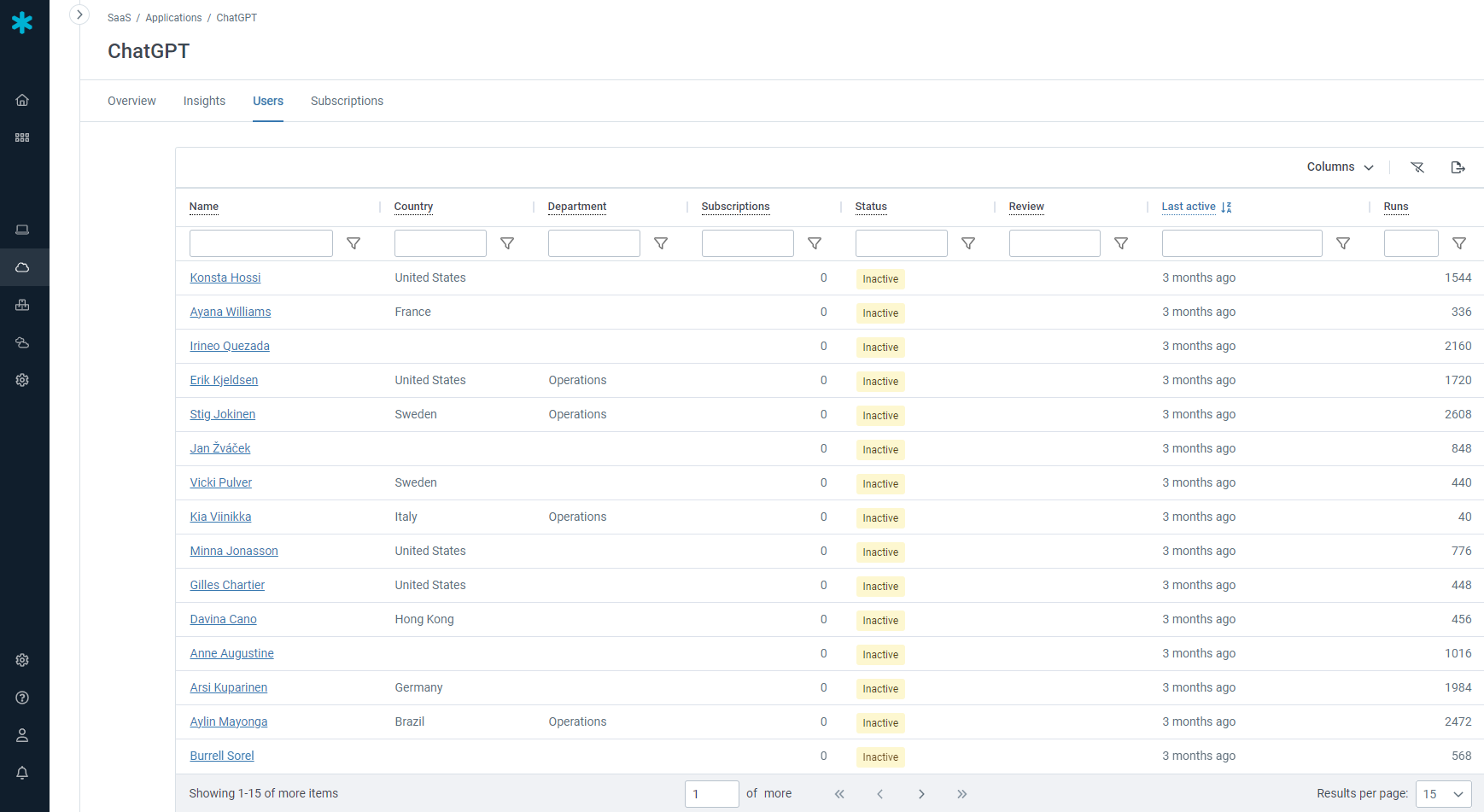
Using the Snow solutions, we found 236 cloud-based applications that both we and the department heads simply didn’t know about, and we even discovered users with illicit gaming software. With Snow, we gain real-time insight into our security risks, software consumption and asset inventory to help the Council make better strategic decisions in support of service delivery.
Frequently asked questions
Shadow IT is any IT asset your IT team does not know about. Technology purchasing has become more distributed with SaaS vendors targeting departmental buyers (CMO, CRO, CTO) and end users via product-led growth initiatives. Broadly speaking, Shadow IT can encompass:
• Applications purchased by individuals
• Enterprise applications purchased by a department/line of business
• Open source or free applications
• Deny-listed applications still being used by employees
• Applications that might be end of life that are still in use
There are multiple ways to discover shadow IT.
• Usage metering: Usage metering helps you identify what applications are actually being used by employees. In addition to understanding last login, you can find details like how many runs over a period of time and average hours/minutes per run to spot heavy vs. infrequent users of applications.
• Cloud access security brokers (CASB): CASBs can identify use of cloud applications, including detecting use anomalies (identifying potential threats like Ransomware), and enforce policies to restrict access.
• Low tech: Using your sleuth skills you can inquire about ‘must have’ applications used in each department. Most of the time, operations teams will have details of the important applications that make their teams successful.
With the proper visibility and policies in place, you can govern it. Procurement can utilize SSO platforms and self-service to make it easy for employees to get what they need, and an inventory of applications by category and department can help crosscheck authorized applications already in use.
Informing IT, Transforming IT
Industry insights to help keep you informed
Let’s get started
Our team is standing by to discuss your requirements and deliver a demo on how to uncover Shadow IT and eliminate risk.