Security and Regulatory Risk Management
Strengthen IT security & regulatory compliance with Flexera
Organizations face an ever-increasing array of risks. From internal audits to regulatory compliance to security vulnerabilities, your IT team needs to identify and remediate risks across a wide range of areas. Solutions that automate data gathering and provide actionable insight are the key to addressing these challenges.
Recommended Products
Improve security and resilience in your outdated or vulnerable software
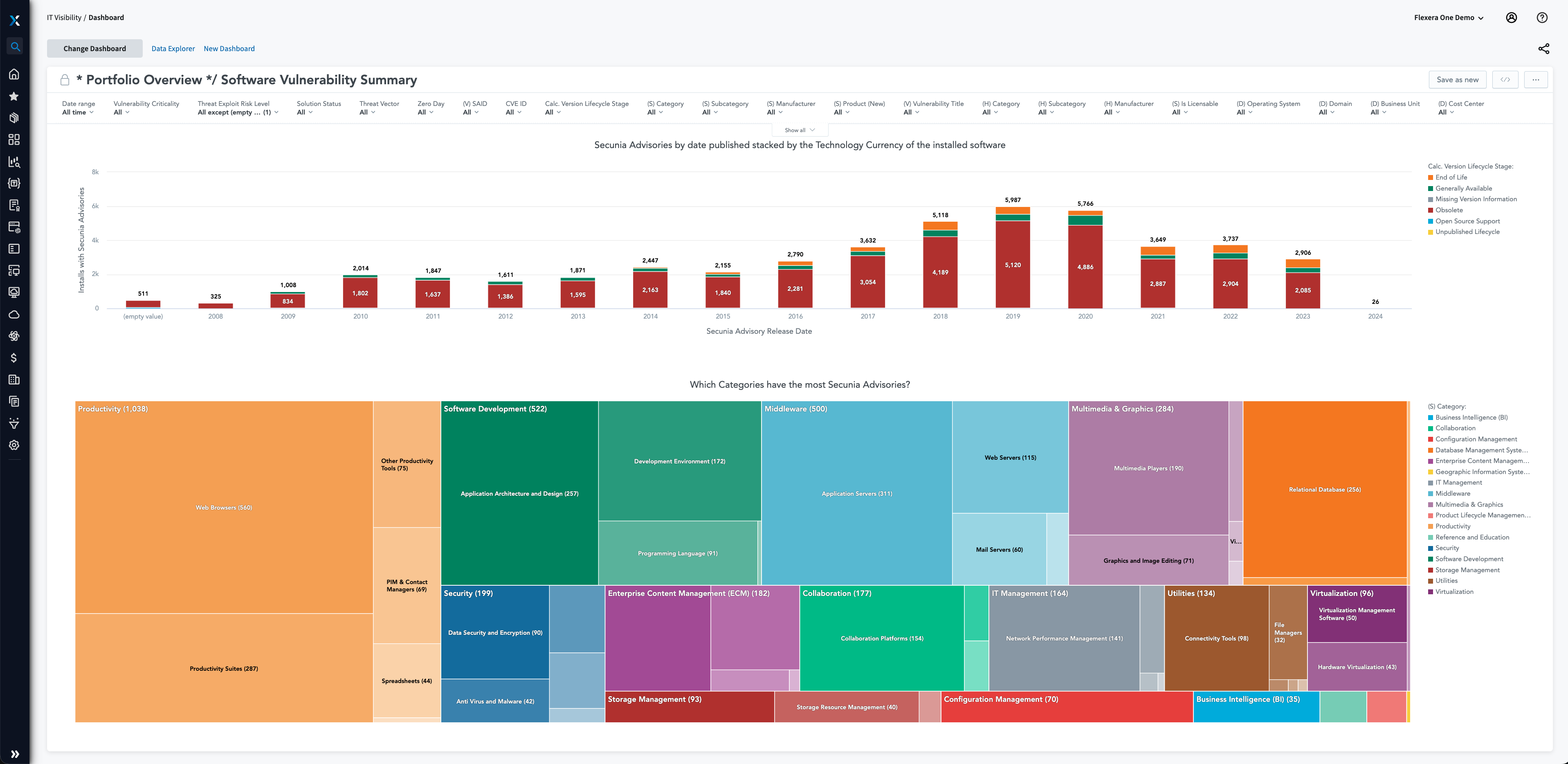
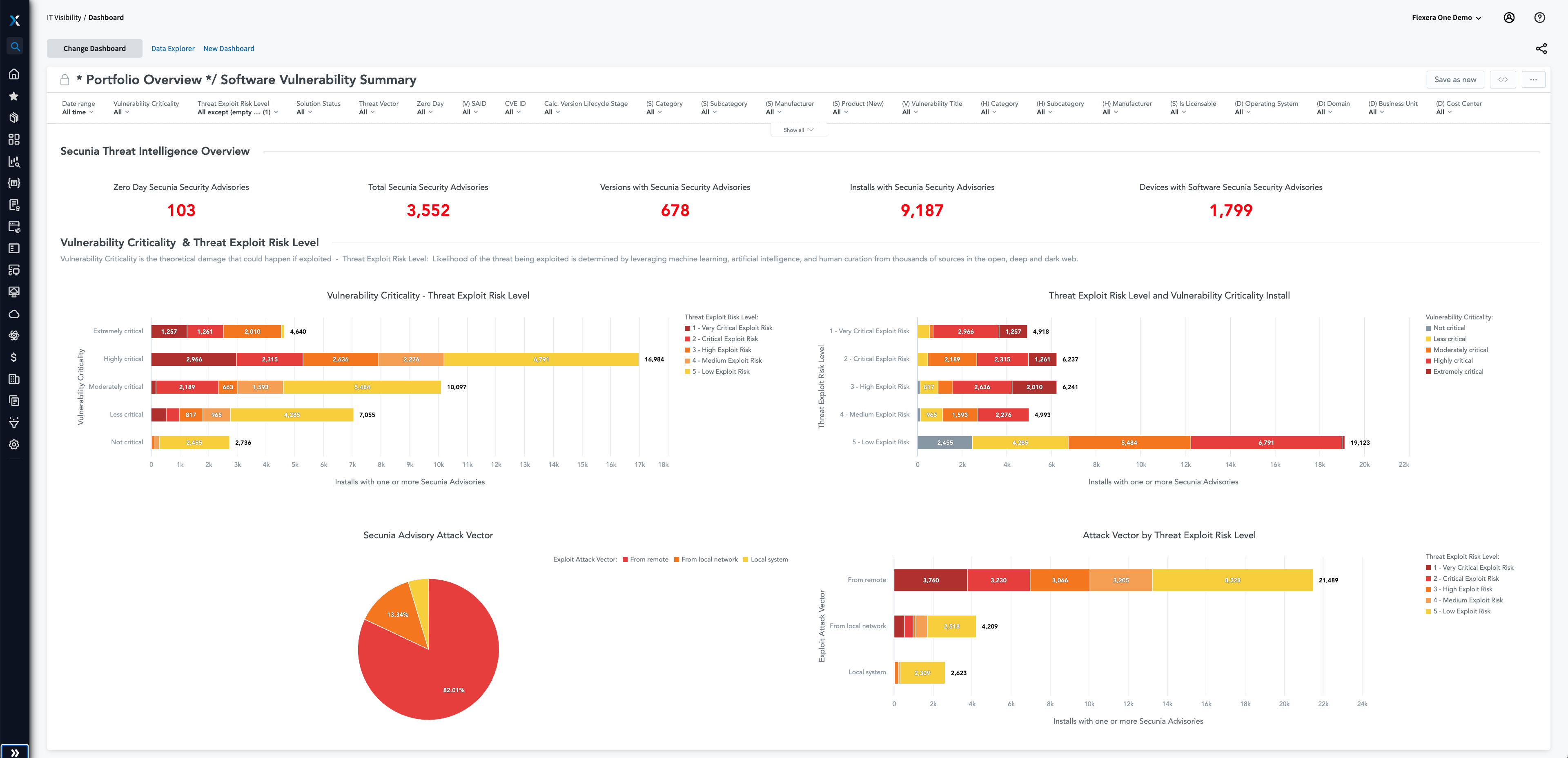
Software vulnerability management
Software vulnerability management
Identify and prioritize software vulnerabilities
Cybersecurity threats are everywhere and constantly evolving; an effective defense strategy starts with visibility. Data and proprietary insights are essential to provide visibility into relationships and dependencies, a prerequisite for effective cybersecurity or risk remediation. Find all known vulnerabilities by identifying which exposed applications are in use and where they reside, as well as the attack vectors. Protect your organization leveraging reliable vulnerability intelligence with robust, contextual data around risks—so you can prioritize which to address first.
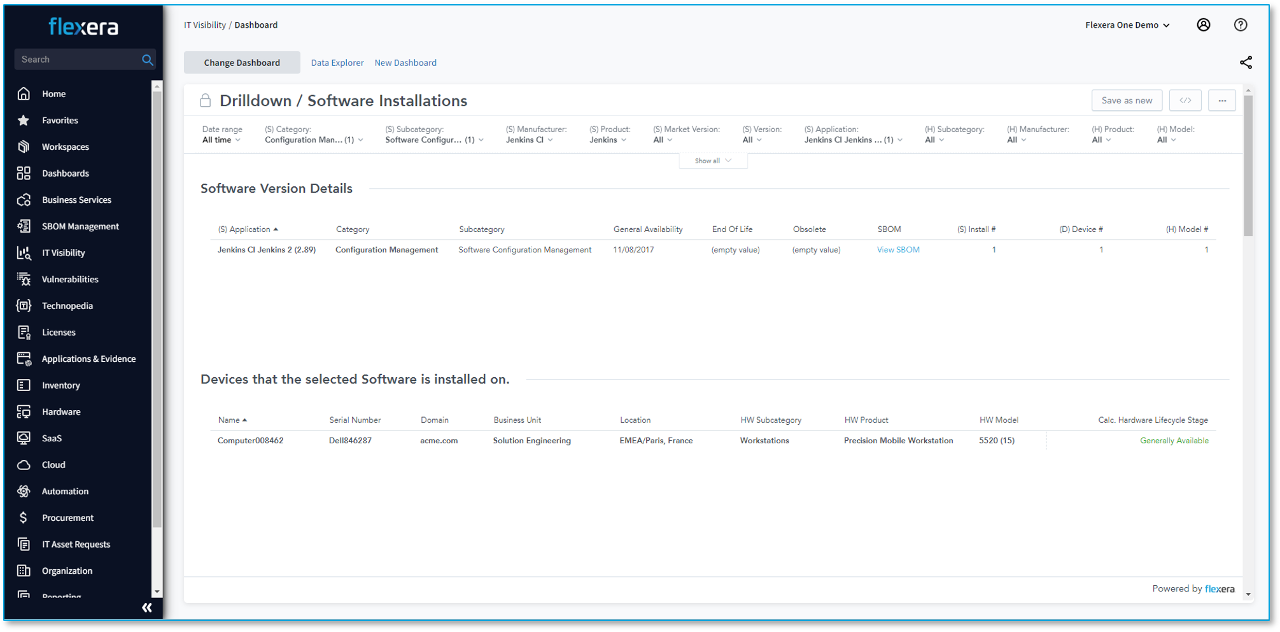
SBOM management
SBOM Management
Reduce risk from software components
Modern hybrid IT infrastructures are loaded with potentially risky third-party elements in the software that powers your most strategic and important applications—including open-source software (OSS) and commercial-off-the-shelf (COTS) components.
Comprehensive software bill of materials (SBOM) management offers you clear visibility and peace of mind through transparency, security and compliance in the software supply chain. With advanced automation, deep scanning and cloud-based accessibility, you can manage software complexities by tracking producers, third-party code and internal modules, aiding in compliance and risk management.
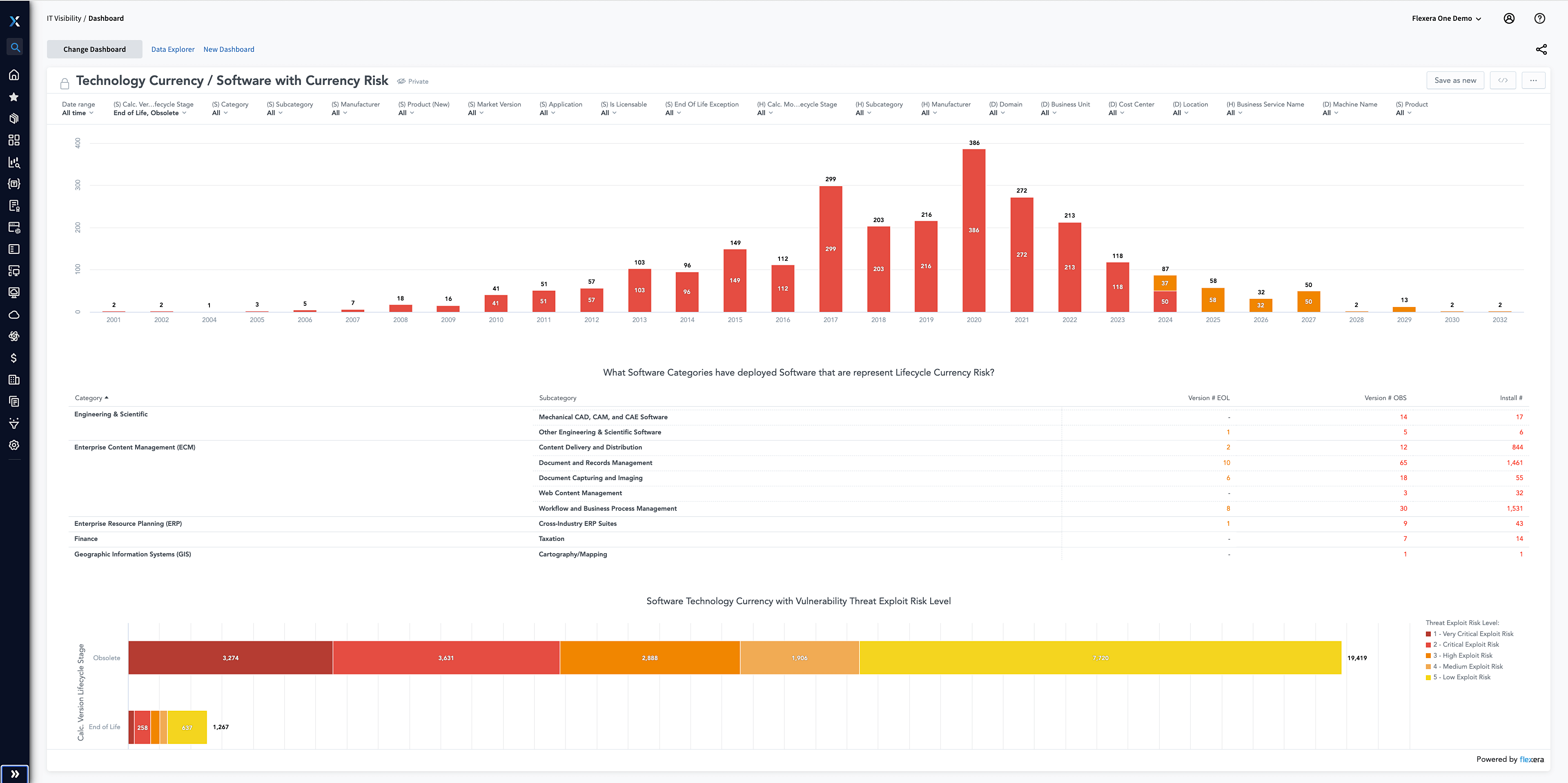
Industry and regulatory compliance
Industry and regulatory compliance
Meet regulatory requirements, save costly penalties
IT regulations are designed to help protect consumer investments and data, establish security guidelines and prevent or mitigate risk. However, these regulatory requirements are often complex, and missteps can be costly.
Meeting compliance requirements that identify and reduce risk is dependent upon reliable intelligence. Proactively plan for security vulnerability remediation, tech debt or obsolescence management in your estate with key data points aligned to your IT estate.
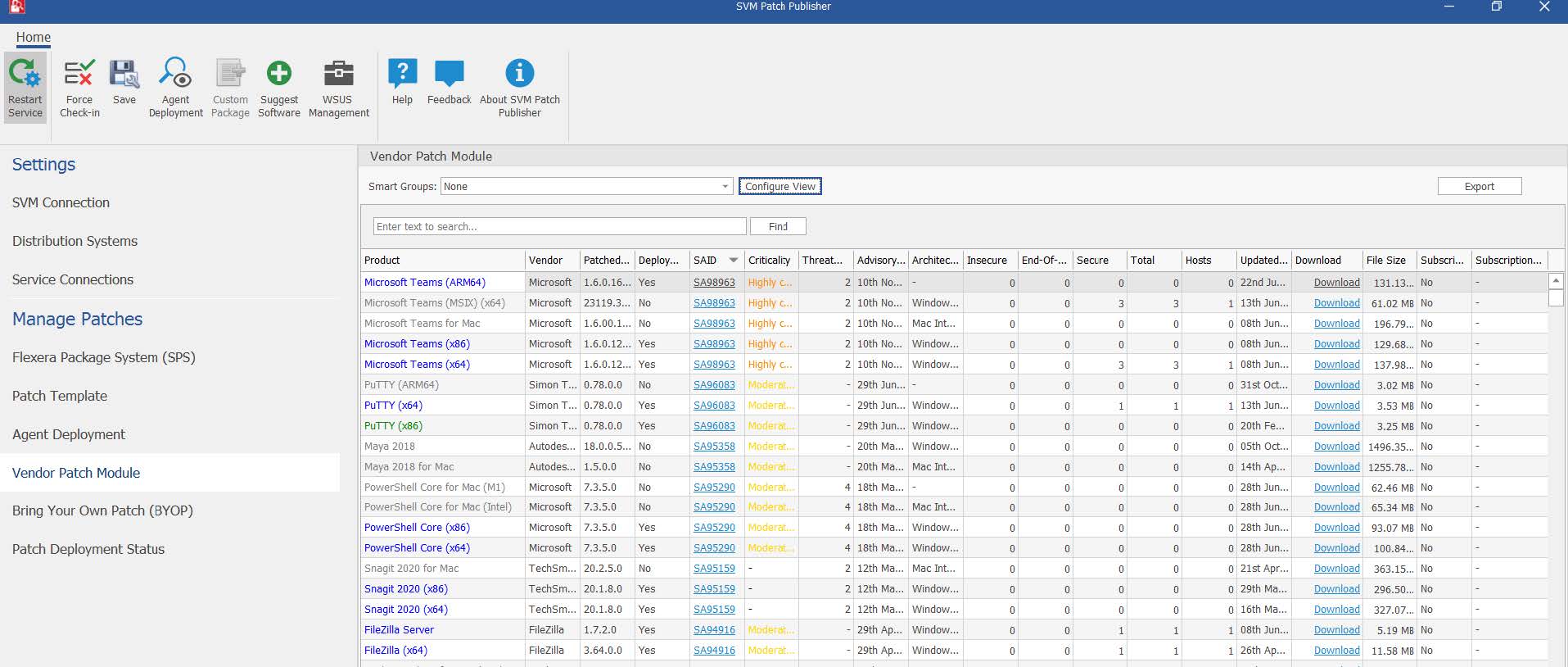
Patch management
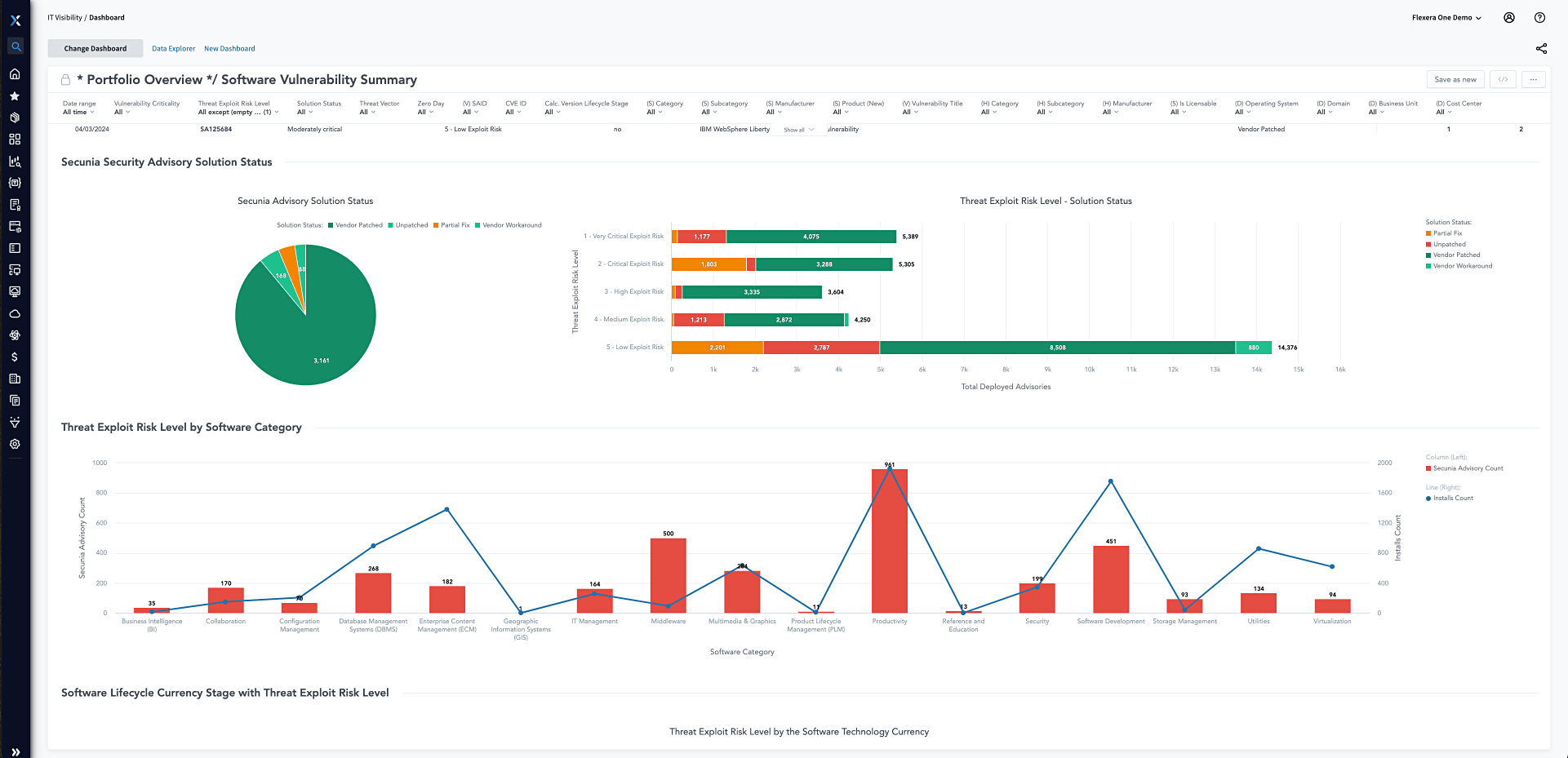
Patch management
Effectively prioritize patching activity
There’s a dangerous gap between the time when third-party software vulnerabilities are disclosed and when they're identified and patched. The volume and risk are too high to push all known patches as quickly as possible. With thousands of patches at your fingertips, assessment and prioritization are requirements.
Prioritize vulnerability remediation activities with a focus on those most likely to be exploited. Leverage threat intelligence scoring built on machine learning, artificial intelligence and human curation from thousands of sources on the open, deep and dark web.

What are the top priorities of the modern IT leader?
33%
Integrating AI
24%
Reducing IT costs
22%
Reducing security risks
Security and regulatory risk management
Flexera helps you adapt to changing IT regulations and security challenges
Industry regulation can present complex challenges for IT professionals. At Flexera, we understand the scope of these challenges. Our customers range from banking and financial industries to healthcare, education, high tech and beyond. All these industries have regulatory bodies that help ensure data of all types are secured against threats, adhering to respective laws and handled with the care and standards necessary to ensure risk mitigation against the organization and their consumers. Flexera provides a continuous pipeline of clean, enriched technology data, powered by Technopedia and Secunia Research, to serve as a source of truth for your enterprise systems and mitigate risk across the organization.
With business adapters sharing data between the tools that drive the engine of [the organization], each set of stakeholders is assured the data they’re using is accurate and consistent across business units.
Frequently asked questions
While both terms indicate phases where support diminishes for a product, they have distinct meanings:
- End of life (EOL): This is the date after which a product will no longer be sold or renewed. However, it might still receive some form of support, such as security patches
- End of support (EOS): This date marks the complete cessation of all support services for the product. After this date, no new patches, updates or fixes will be released, even for critical vulnerabilities
To learn more, see our glossary here.
- Security implications: Products past EOL/EOS are no longer updated, making them susceptible to potential threats, cyberattacks and vulnerabilities
- Operational challenges: Relying on outdated products can lead to inefficiencies, compatibility issues and augmented operational costs
- Regulatory compliance: Many industry standards and regulations mandate the use of supported and updated software, emphasizing the importance of tracking EOL and EOS dates
IT visibility is the ability to have a comprehensive, real-time insight into an organization's entire IT estate. This encompasses everything from traditional on-premises hardware and software to cloud-based services, SaaS applications, and more. For more information, see our glossary here.
Informing IT, Transforming IT
Industry insights to help keep you informed
Meet regulation and reduce risk
Deliver definitive data to drive down technology risk, effort and costs